Juice Jacking Attack: Scammers are Stealing Data Through Public Chargers
Last Updated : 04 Mar, 2024
 1.26L
1.26L

Sarah checks into a busy airport. She is early into the airport, and the boarding is yet to start. Sarah is casually strolling through Instagram when her phone beeps “Low Battery”. She plugged into a “free” charging station, not knowing it was a trap for a juice jacking attack. Unbeknownst to her, hackers extracted the data from her phone, leaving her high and dry before the dark web. Sadly, she learned the hard way: security comes before convenience.
Juice jacking is a form of cyber attack targeting phones and other devices tethered to public charging stations. Scammers utilise public charging outlets, often found in airports, cafes, and other convenient spots, to break into tethered smartphones. Many domestic and international agencies, including the FBI, have issued warnings against cybersecurity dangers associated with using public charging stations.
This blog sheds light on how does juice jacking work and measures to stay protected from these attacks.
What Is Juice Jacking?
So, what exactly is Juice Jacking? Well, it’s a sneaky trick scammers use to extract data from devices when you plug your device into a public charging station.
Scammers have got two main tricks up their sleeves for the juice jacking attack: tampered hardware and crafty software.
Cybercriminals tamper with the hardware of the charger USB port to install bots or malware into the mobile phone. Once the malware is installed, it can monitor your keystrokes or extract sensitive information to hand over to the hackers.
Now that we know what juice jacking is, let’s dive into the nitty-gritty of how these attacks work.
Did You Know?
The term “juice jacking” was first coined in 2011 by investigative journalist Brian Krebs.
How Juice Jacking Works?
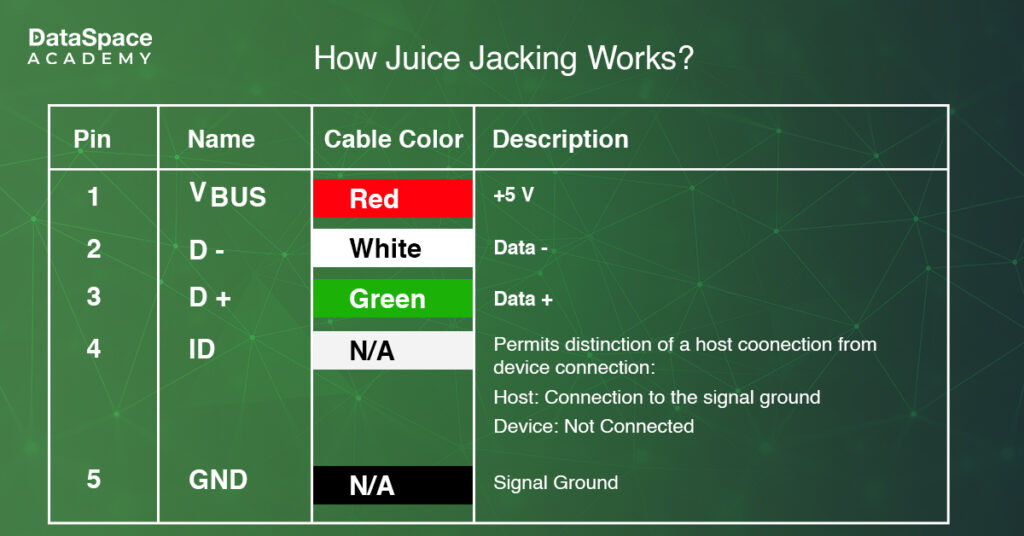
A USB port carries five pins:
- 1 for power
- 2 for transferring data
- 2 for indicating device presence and ground
When a phone is plugged in via USB, the power pin charges the device. However, hackers can manipulate the data transfer pins for data theft. Once the connection is established between a phone and a computer system, the scammers can access, modify, or copy files from the phone.
Worse, hackers can inject malware into the phone via these tampered charging stations. Once the malware is installed, it can spy on your activities and cause all sorts of trouble for you.
Join our cyber security courses online to learn in detail about how these attacks work.
Potential Consequences of Juice Jacking
The dangers of Juice Jacking go far beyond the inconvenience of a low battery. Let’s explore the potential consequences of falling victim to this cyber threat:
- Data Theft and Data Breaches: When hackers successfully execute a Juice Jacking attack, they gain access to your personal information. This can include sensitive data like passwords, credit card details, and private messages.
- Identity Theft and Financial Loss: With your personal information in their hands, cybercriminals can impersonate you, leading to identity theft. This can result in financial losses, damaged credit, and a long, painful process of reclaiming your identity.
- Ransomware Attacks: In some cases, Juice Jacking can infect your phone with ransomware. This malicious software can lock you out of your device and hold your data hostage, demanding a hefty ransom for its release.
- Privacy Invasion: Hackers could gain unauthorized access to your device’s camera and microphone. These illicit actors might invade your privacy and potentially record your personal life without your knowledge.
- Social Engineering Attacks: Juice jacking exposes your contact list and personal information to cybercriminals. They can further exploit these confidential details to launch social engineering attacks that could risk the data privacy of your near ones. Scammers can manipulate your friends, family, or colleagues into revealing sensitive information or falling for scams.
- Loss of Reputation: The data stolen by hackers can not only compromise your financial security but your reputation as well. Juice Jacking can tarnish your reputation, both personally and professionally by exposing your sensitive information to the public.
- Emotional Anxiety: Violation of your privacy, coupled with financial loss, and loss of reputation, can lead to emotional distress and anxiety. These toxic factors could eventually impact your overall well-being.
Precautions to Protect Yourself

Now that we’re aware of the perils of Juice Jacking, let’s get down to the business of keeping your precious data safe. Here are some simple yet effective precautions for preventing juice jacking.
- Bring Your Charger: The safest way to charge up “safely” is by using your personal charger. It might take a few extra seconds to untangle those wires, but it’s well worth it to avoid potential data theft.
- Carry a Portable Power Bank: These nifty gadgets are lifesavers. They let you charge your device on the go without plugging into any public outlets. It’s like having a pocket-sized power station in your bag.
- USB Data Blockers: Invest in these compact adapters that only allow power flow, not data transfer. They act as a digital bouncer, keeping your information locked away from prying eyes.
- Disable Auto-Connect: This is one extremely crucial tip for juice jacking protection. Turn off automatic connection settings on your devices. This way, they won’t automatically connect to unfamiliar charging stations, giving you more control.
- Use Secure Networks: Stick to trusted and secure Wi-Fi networks for data-sensitive activities. Avoid open and unsecured networks since hackers can easily intercept them to extract sensitive information. You will learn more about these security tips with our industry-leading cyber security course.
- Regular Software Updates: Keep your device’s software up-to-date. Updates often include patches for known vulnerabilities, making it harder for cybercriminals to exploit them.
- Opt for “Charge Only” Mode: When your device prompts you to choose a USB connection option, select “charge only.” This prevents data transfer during charging sessions.
It’s not just about charging your device; it’s more about safeguarding your digital life.
Wrapping up
Sarah learned a lesson the hard way.
But you don’t have to.
Our phone holds the most intimate details of your life. And, scammers taking over your device could be devastating. You need to protect it from scammers at any cost. All you need to do here is to be aware and follow a few simple safety steps while charging your phone in a public campus. By staying informed and cautious, you not only protect yourself but also contribute to keeping your friends and family safe.
 1.26L
1.26L





































































































