A Beginner’s Guide to API Penetration Testing
Last Updated : 21 Aug, 2024
 66.14K
66.14K

Introduction
API channels serve as the gateways to 83% of web traffic flows. Thus, ensuring API security is a must for organisations to facilitate seamless interaction between websites and visitors. But did you know that almost 94% of the organisations have hidden vulnerabilities in their APIs? Hackers are always sniffing out for vulnerable APIs and lack of cyber defense could lead to devastating consequences. This is where API penetration testing comes to the rescue.
If you are new to the API pentesting world, here is your absolute guide.
What is API Penetration Testing?
API penetration testing is the process of verifying application security by emulating the attack methodology of real hackers. Pentesting helps to detect vulnerabilities, flawed configurations, and designs so that they can be addressed immediately before hackers can get to them.
In other words, security testing for API builds the first line of defense for API channels in the battle against cyber attackers.
API pentesting within the SDLC (software development lifecycle) is the cornerstone of maintaining and updating an organisation’s overall cyber security health.
What do API Pentesters do?
During an API security testing, a pen tester performs the following functions:
- Discovering hidden API endpoints
- Analysing the authentication and authorisation models used by APIs
- Identifying and testing injection vulnerabilities like SQL, NoSQL, and command injection
- Checking the flow of incoming data and its sanitisation process
Some popular api security testing tools include Burp suite, Nmap, Akto, Postman, and ZAP.
Importance of API Pentesting
API penetration testing is primarily conducted to secure integrated business applications for immuning the API channels from potential vulnerabilities. Regular API pen testing empowers organisations to significantly reduce the risks of potential breaches, and also comply with security standards.
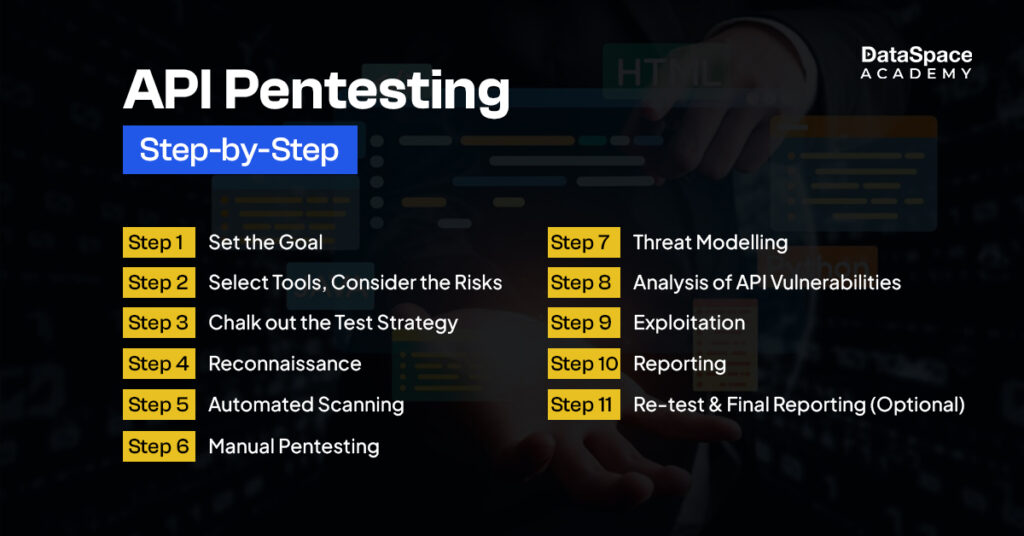
Steps of API pentesting
API or mobile app pentesting involves a combined strategy of automated scanning and manual testing for generating accurate and detailed security reports.
- Goal setting
Goal setting helps to chalk out to the direction of executing the test. This includes specification of scope, identification of API flaws, budget allotment, and the timeline within which the API testing is to be executed.
- Deciding the scope
- User roles
- API Documentation
- Valid responses and API calls
- List of restricted and sensitive API endpoints
- Swagger, postman, and documentation in the API endpoints
The scoping phase involves selecting appropriate tools and creating a detailed test strategy. This also encompasses evaluating risks, assumptions, schedules, and other key factors such as:
- Reconnaissance
This stage is about finding sensitive information such as forum posts, user manuals, and usernames that are essential and useful in the testing stages. The phase also includes reviewing API documentation to understand the functionalities of API and determining the attack surfaces.
- Automated scanning
Automated scanning is executed by specialised tools designed for quick identification of common vulnerabilities like SQL injection, broken authentication, and insecure endpoints. This phase helps detect security flaws efficiently, setting the stage for more in-depth manual testing.
- Manual penetration testing
The process involves hands-on techniques to uncover vulnerabilities that automated tools might miss. This process includes assessing endpoints, manipulating requests, and analysing responses to identify security flaws – such as authentication bypasses, insecure data handling, and logic vulnerabilities.
- Threat modelling
The threat modelling phase is essential for identifying potential threats, attack types, and their probabilities. This helps prioritise risks and uncover vulnerabilities. It involves manually reviewing exposed endpoints to assess attack surfaces and unauthenticated business functions.
- Analysis and detection of API vulnerabilities
After the pentester has enumerated and identified the resources and vulnerabilities in the API, it is important to scan the vulnerabilities at the application and network layer. The tester also needs to identify the vulnerabilities that exist and keep a note of the vulnerability confirmation and manual identification of endpoints.
- Exploitation
Further, pen testers utilise different tools to gain an understanding of unauthorised access to the APIs. This helps them to escalate privileges and also penetrate into the API.
- Reporting
Post exploitation, pen testers document comprehensive reports of the findings derived from the testing phase. The report also provides recommendations regarding remediation of the vulnerabilities that are identified during the testing process.
- Re-test & Final Reporting (Optional)
Pen testers conduct re-testing for further clarification, if needed. The re-test stage is followed by final reporting.
Benefits of API penetration testing

Some of the major benefits of API penetration testing include the following:
- Early Vulnerability Detection
Uncovers weaknesses before attackers can exploit them, allowing for timely remediation and reduced risk exposure.
- Enhances Security Posture
By simulating real-world attacks, penetration testing improves overall security practices to protect sensitive data and systems.
- Ensures Compliance
Regular testing helps pen testers meet industry regulations, ensuring that APIs comply with security standards that might otherwise lead to potential legal issues.
- Improves Incident Response
Allows organisations to strengthen their ability to detect and respond to security breaches effectively.
- Boosts Customer Confidence
Demonstrating a commitment to API security through penetration testing builds trust with clients and stakeholders.
Conclusion
The API penetration testing is mandatory preventive approach that every online business must prioritise before it’s too late. The process ensures the protection of businesses from any sort of cyber threat by utilising manual and automated API scanners. DataSpace Academy’s penetration testing certification covers various types and methods of penetration testing, offering both theoretical insights and hands-on experience to master the processes involved in effective cybersecurity assessments.
 66.14K
66.14K




































































































