Penetration Testing Guide - Phases, Types, Benefits, and Scope
Last Updated : 13 Feb, 2024
 1.31L
1.31L
Introduction
Every 39 seconds an account is being hacked. The rate of cyber crimes spiked up by a whopping 61% in 2022 from 2016. Cybercrimes impact around 80% of the businesses, making it inevitable for businesses to introduce better cybersecurity measures. This is where Penetration Testers come to the scene. These security professionals shoulder the responsibility of building a mighty defense and protecting business data from cyber criminals. With cyber crimes on the rise, there is an increasing scope of penetration testing, creating a huge demand for pentesters. Put simply, pentesting is one of the most promising careers today. If you are aspiring for a rewarding career in pentesting, here is the ultimate penetration testing guide for you.
Crafted for aspiring security professionals, the blog aims to shed light on all the major aspects of penetration testing for a comprehensive walk-through.
Overview of our penetration testing guide
Penetration testing launches a simulated attack on the computer system, applications, and network to identify vulnerabilities which can be exploited by the hacker. Performed by ethical hackers, the procedure is aimed to protect the target system from black-hat hackers – by detecting the problem areas beforehand.
Findings reported by pentesters help the security teams to stay aware of the warning signs and improve the security posture of the organisation.
Pentesters are responsible for abiding by the regulatory compliance of data security such as General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA)- in order to ensure the mandate of security controls.
Phases of Penetration Testing

The process of penetration testing can be categorised into the 5 phases which include the following:
- Reconnaissance
- Scanning
- Gaining access
- Maintaining access
- Remediation and clean up
This is the first stage of penetration testing where pentesters work to gain details of the target system. In this stage, the professionals define the goals and scope of the test, systems to be tested, and the techniques to be deployed. The stage of reconnaissance also includes an approach of gathering intelligence such as from domain name, mail server and networks. This is important to understand the way in which a particular target works and the potential vulnerabilities it might harbour.
This is the second stage where the penetration testers attempt to comprehend the overall response of the target system. They look for the weak areas such as open services, open source vulnerabilities, and problems of application security.
The scanning process is carried out in two ways – static analysis and dynamic analysis.
The static analysis is the process of inspecting the code of an application for estimating how the application may behave while running. The dynamic analysis focuses on inspecting the code of application in the running state. Compared to the static one, the dynamic one is considered to be a more practical approach to scanning. This also provides the real time overview of the performance of the application.
In the third stage, the tester launches simulated web application attacks such as SQL injection, backdoors and XSS into the target system. The pentesters deploy multiple penetration testing techniques to exploit vulnerabilities to gain access to the target system. This step helps them to determine the scale of damage the target system might encounter in case of a hacking attack.
This step is majorly about maintaining the access after gaining access. This is the process where simulated attacks need to be aligned for a particular duration for data removal and data modification. The goal is to check the respective weaknesses to gather a continuous and persistent presence across the system that has been exploited.
In this stage, pentesters attempt for in-depth access and imitate advanced persistent threats for extracting the sensitive information.
This is the last stage of penetration testing. This is where pentesters clear up traces and artefacts that are used during the testing phase. The stage is important to ensure that the traces are cleaned so that it can’t be leveraged by the real attacker in future. This enables organisations to make necessary changes so that they can close the security loopholes in security infrastructure.
Areas where penetration testing is done
Even though there has been an increase in the cases of cybercrime, not many organisations recognize the overall critical role which is played by penetration testers in maintaining a secure cyber security strategy. The proactive identification of the weaknesses that can be easily exploited, the professionals can reduce overall chances of cyber security or data breach incidents. Penetration testing also includes the approaches uncovering overall vulnerabilities in the form of unsanitized inputs. Thes are in turn susceptible to code injection attacks.
On the basis of goals of penetration testers and the areas of vulnerabilities to be exploited by them, the penetration testers are provided with the necessary information so that they can come up with an awareness strategy. Based on the degree of vulnerabilities, the penetration testing is done on physical assets, network services, wireless services and applications. Penetration testing also includes API testing as well as physical testing of the security postures.
Types of penetration testing
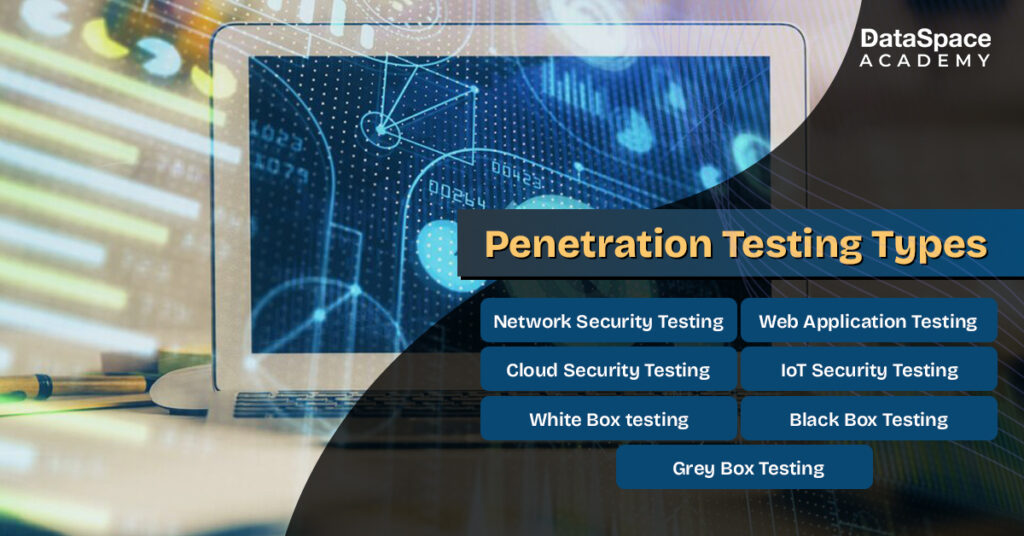
Here is a brief on the major types of penetration testing:
- Network security testing
- Web application testing
- Cloud security testing
- IoT security testing
In network security testing, the pentesters are responsible for uncovering and exploiting the vulnerabilities existing in the network. This is also about discovering security loopholes in the various allied devices such as switches, network hosts and routers. Network security testers aim to exploit flaws in the form of misconfigured assets, weak passwords, to secure critical data or systems.
Web application penetration testing focuses on testing the potential application security risks including authorization, authentication and coding errors.
In this case, security professionals work with third party cloud providers to execute cloud-based security testing. This includes validating security parameters for the cloud deployment to identify likelihood and risks of the vulnerabilities. The pentesters also provide recommendations for the overall improvement of the cloud environment.
The IoT security testing uses the approach of layered testing so that the penetration testers are able to spot the weaknesses.
Penetration testing is also classified into the following types:
- White box testing
- Black box testing
- Grey box testing
In the white box testing, the penetration testers are provided with the complete knowledge of the target system. The shared information includes details such as credentials, source codes, and network diagrams.
In the black box testing, the penetration testers are not provided with any information about the target system. They have to completely rely on their own plan in order to develop the attack. The pentester would also need permission to perform the reconnaissance phase in black box testing.
The grey box testing uses a mixture of black box and white box testing strategies. In this case, pentesters receive limited information about the target. Also, they do not have the roadmap of the pertinent system and network information.
You can sign up with DataSpace Academy’s penetration testing course to learn multiple types of pentesting.
Significance of penetration testing
When it comes to benefits of penetration testing, businesses count on pentesters to improve the overall security posture.
It is important to carry out pentesting for ensuring consistent network security and IT security management practices. This helps in early detection of newly discovered threats so that these glitches can be mitigated at the earliest. Penetration testing is also important to assure compliance with regular mandates as per industry standards.
Career scope of penetration testing
The demand for security professionals and penetration testers has remained high in recent times. Most importantly, with the rise of cyber crimes, the demand is expected to escalate in the coming times as well.
Likewise, the pentesters earn a generous package, ranging around ₹ 6.0 Lakhs to ₹ 18.7 Lakhs. Also, pentesters are highly sought-after in a wide range of industries, including tech, health, banking, insurance, media, and more. These professionals will find high-paying jobs in government departments as well to fight cybercrime profiles.
Conclusion
Hope this blog will help you to attain a substantial understanding of both the technical and career spectrums of penetration testing. If you are aiming to build a career in an exciting, high-paying, and sustainable domain, pentesting would be a great option.
You can sign up with DataSpace Academy for both pentesting and advance penetration testing course programs to build a career in pentesting.
 1.31L
1.31L





































































































