Phishing Attacks: Overview, Types, and Prevention Tips
Last Updated : 18 Oct, 2023
 1.25L
1.25L

Introduction
Imagine this: You receive an email from your bank, urgently notifying you of a potential security breach. Your heart skips a beat as you read the alarming message, prompting you to click on a link to resolve the issue immediately. Fear and concern grip you, urging you to act swiftly to protect your hard-earned money and personal information.
But wait. Take a step back. What if that email isn’t from your bank at all? What if it’s an intricately woven web of deceit spun by a cunning cybercriminal?
Welcome to the world of phishing attacks – a treacherous digital landscape where innocent clicks can lead to disastrous consequences!
What Exactly is a Phishing Attack?
Well, phishing attacks have become a prevalent and sophisticated hazard, targeting individuals, businesses, and organisations alike. These attacks are malicious attempts to deceive individuals into providing sensitive information, like passwords, credit card numbers, or personal data. Worse, phishing attacks can be too subtle to detect – these deceptive tactics can trick even the most vigilant among us.
Phishing attacks rose to a whooping 500 millions+ in number back in 2022. With these cyber scams on the rise, business organisations are looking for certified cybersecurity professionals who can protect their network from the phishing scammers. One of the most in-demand careers today, cybersecurity also extends a lucrative pay package. If you are aiming to build a career as a certified cybersecurity analyst, you can check out the Master Program in Cybersecurity by DataSpace Academy. The course provides training by industry experts and also offers internship opportunities, soft skill development, and placement assistance.
Types of Scams Caused Due to Phishing Attacks
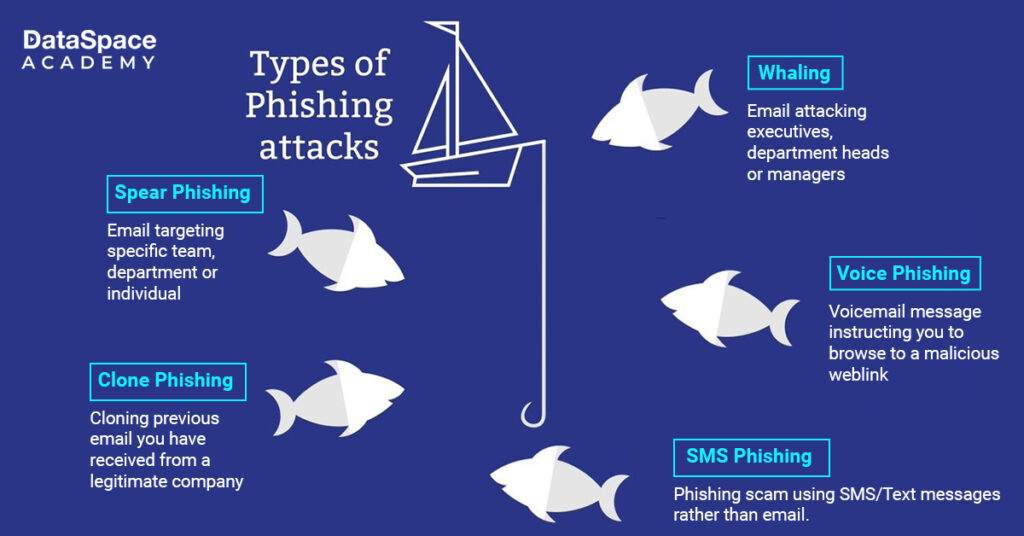
Here are some of the major variants of phishing attacks, along with precautions to help prevent them.
-
Email Phishing
What is it?
Attackers send deceptive emails to a large number of recipients, impersonating legitimate organisations or individuals. These emails typically contain malicious links or attachments. Once clicked upon, these links lead to a virus-laden site which is designed to steal personal information of the recipient.
Sources of Attack
Phishing emails can be sent by cybercriminals who use techniques like email spoofing to make the emails appear genuine.
Precautions to Ensure Prevention- Be cautious of unsolicited emails, especially those requesting personal information or urging urgent action.
- Verify the email sender’s identity; check for spelling and grammar errors. Try not to click on skeptical links.
-
Spear Phishing
What is it?
Unlike regular phishing scams, spear phishing targets specific individuals or organisations. Attackers gather personal information about their targets to create highly customised and convincing emails. These seemingly benign emails are designed to trick the recipient into unknowingly revealing sensitive data.
Sources of Attack
Attackers often gather information about their targets from publicly available sources, such as social media. They can also launch data breaches to tailor their phishing attempts.
Precautions to Ensure Prevention- Exercise caution with emails specifically tailored to target you or your organisation.
- Double-check email addresses and domains; be wary of requests for sensitive information. Always verify (unbiasedly) any unusual requests made by email.
-
Smishing (SMS Phishing)
What is it?
This type of phishing attack involves sending fraudulent text messages to targets’ mobile phones. Smishing messages often contain enticing offers, urgent requests, or prompts to click on malicious links. By doing so, the recipients are directed to phishing websites or tricked into disclosing personal information.
Sources of Attack
Cybercriminals use automated systems or tools to send bulk SMS messages for Smishing. They usually obtain the target through various illegal means, such as data breaches or other illicit activities.
Precautions to Ensure Prevention- Be sceptical of text messages from unknown senders, especially those containing urgent requests or offers.
- Avoid clicking on links in SMS messages from unknown sources.
- Avoid providing personal information via text unless you have confirmed the sender’s identity.
-
Vishing (Voice Phishing)
What is it?
Vishing is a type of phishing conducted over phone calls. Attackers impersonate legitimate organisations or individuals to deceive recipients into revealing sensitive information or performing certain actions, such as transferring funds or providing access to systems.
Sources of Attack
Attackers may use techniques like caller ID spoofing to manipulate the displayed phone number, making it appear as if the call is from a trusted source. They can obtain personal information from public directories, social engineering tactics, or data breaches.
Precautions to Ensure Prevention- Be cautious of unsolicited phone calls requesting personal information or offering unexpected benefits.
- Avoid providing sensitive information over the phone unless you initiated the call or are certain about the caller’s identity.
-
Pharming
What is it?
Pharming involves redirecting users to malicious websites without their knowledge or consent. Attackers manipulate DNS (Domain Name System) servers or compromise routers to redirect legitimate traffic to fraudulent websites that mimic trusted ones. Once users reach those malicious sites, they are manipulated to enter (unknowingly) their confidential data.
Sources of Attack
Attackers may exploit vulnerabilities in DNS servers, compromise routers, or use malware-infected systems to carry out pharming attacks.
Precautions to Ensure Prevention- Ensure that your computer and devices have up-to-date antivirus and anti-malware software.
- Verify the website’s legitimacy by checking the URL for discrepancies or using trusted bookmarks.
- Avoid clicking on suspicious links or pop-ups.
-
Whaling (CEO Fraud)
What is it?
Whaling targets high-profile individuals, typically executives or individuals holding an esteemed designation within an organisation. Attackers craft sophisticated emails that appear to be from CEOs or other top-level executives. These emails usually request for urgent actions such as wire transfers or sharing sensitive data. The goal is to create urgency and force employees (deceptively) into complying with fraudulent requests.
Sources of Attack
Attackers research and gather information about executives from publicly available sources, company websites, and social media. They can also manipulate an insider to derive insights.
Precautions to Ensure Prevention- Implement strict email security measures, including Multi-Factor Authentication (MFA), Sender Policy Framework (SPF), Domain-Based Message Authentication, Reporting, and Conformance (DMARC).
- Educate executives and employees about this type of attack and establish protocols for sensitive transactions.
-
Malware-Based Phishing
What is it?
Malware-based phishing involves sending emails or messages that contain malicious attachments or links. When opened or clicked, these attachments or links download malware onto the recipient’s device. Once the malware gets loaded, it starts to capture sensitive information, log keystrokes, or give remote access to the attacker.
Sources of Attack
Cybercriminals distribute malware through various means, including email attachments, infected websites, and compromised software. They can also deploy social engineering techniques that entice users to click on malicious links.
Precautions to Ensure Prevention- Your antivirus software, OS, as well as all applications, must be upgraded with the latest patches.
- Be cautious of downloading files from untrusted sources or clicking on suspicious links.
- Regularly scan your devices for malware.
General precautionary measures to stop phishing attacks
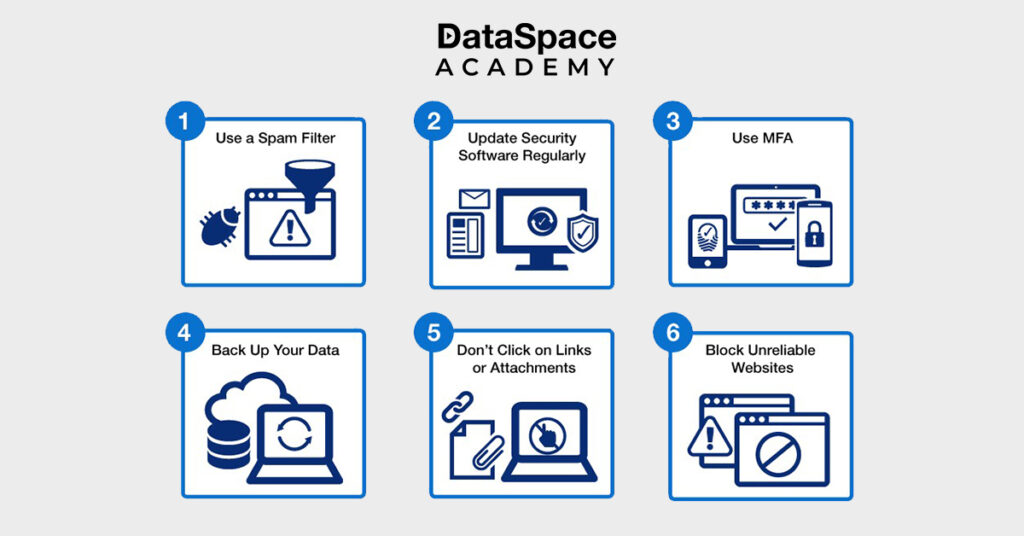
Here is a curated list of phishing attack prevention tips that will help you to keep these scams at bay-
- Always use unique, hard-to-decipher Passwords. A credible password manager would also come handy.
- Enable Multi-Factor Authentication (MFA) whenever possible.
- Keep your operating system, software applications, and web browsers updated on a regular basis.
- Be cautious when sharing personal information online or with unknown sources.
- Educate yourself and your employees about phishing techniques and how to identify them.
- Use reputable security software and firewalls to protect your devices.
- Regularly monitor your financial accounts and credit reports for suspicious activities.
- Report phishing attempts to the relevant authorities or organisations being impersonated.
- Check the URL of every website you visit. Make sure it features “HTTPS” instead of “HTTP”.
Conclusion
It’s important to note that these attacks can originate from anywhere globally, as cybercriminals often operate across international boundaries. They may use a combination of techniques, social engineering, and technological exploits to carry out their phishing campaigns. Remember, constant vigilance and maintenance of healthy cybersecurity practices are crucial in protecting yourself and your sensitive information from phishing attacks.
 1.25L
1.25L




































































































