USB Attacks: Definition, Types, and Tips for Mitigation
Last Updated : 23 Aug, 2023
 1.12L
1.12L

The year was 2009. The first block of Bitcoin came into existence and Barack Obama was sworn in as the 44th president of the United States. Amidst these groundbreaking changes, the world woke up to the news of a high-profile scandal – the Stuxnet – a devastating virus attack on the nuclear program of Iran. According to the reports, an employee at the Natanz uranium enrichment plant allegedly ran USB attacks into the control system. Once inserted, the virus-laden (Stuxnet) USB destroyed the uranium centrifuges and derailed the entire nuclear program.
A removable USB driver is usually the default tool for sending and receiving data. But threat actors often use this small, unsuspecting device to run cybersecurity threats. They prefer using removable media devices for establishing remote connectivity, extracting data, or overtaking the system. And often these incidents can lead to serious financial losses. According to an estimate, in 2023, data breaches cost an estimated $4.45 million (Source: 2023 Cost of a Data Breach Report | IBM).
Undoubtedly, USB drives are essential tools but you need to be cautious. The blog here will discuss how to stay safe from bad USB attacks.
What is USB Attack?
This one is simple. It is the transmission of malicious software through USB devices. Also known as the USB drop attack, here the cybercriminals coax the victim to insert an infected USB drive into their computer. Once the USB drive is plugged into the device, the malware is automatically installed. The not-so-harmful malware variants can trigger popup ads in your system or redirect your browser to unfamiliar sites. On the other hand, dangerous kinds can encrypt your system and demand a ransom for unlocking them.
Understanding USB Attacks
In USB attacks, hackers gain unauthorised entry into computer systems, stealing sensitive information, causing disruptions, or manipulating data for malicious purposes. Researchers have listed 29 types of USB attacks broadly divided into four categories. Here is a listicle of some of the most destructive USB exploitation methods:
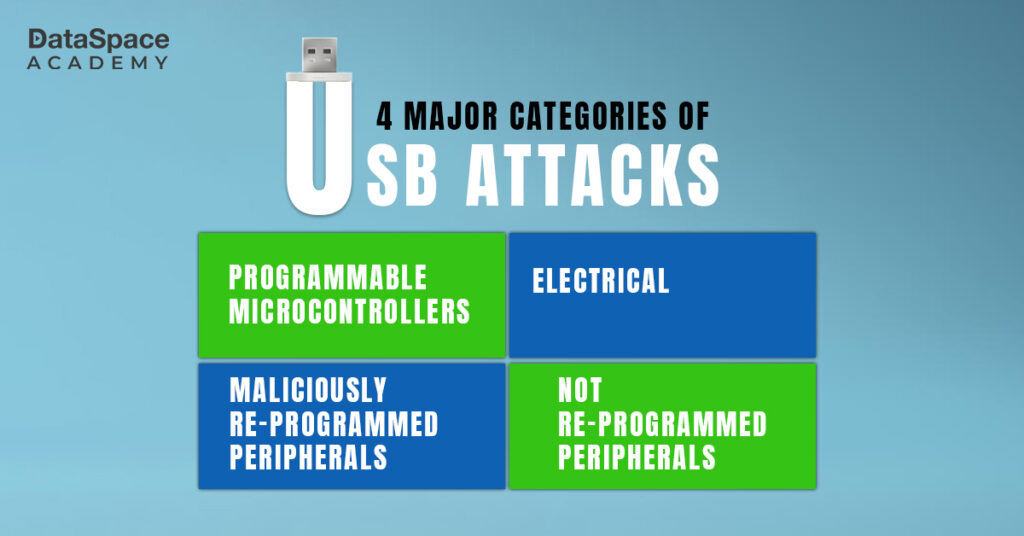
-
Reprogrammable Micro-controller USB attacks
-
USB Rubber Ducky
The USB Rubber Ducky is a keystroke injection attack and resembles an HID (Human Interface Device). When plugged into a computer, it poses as a keyboard, executing a preset sequence of keystrokes to extract sensitive information. Worse, most well-known antivirus programs and firewalls are unable to detect this device.
-
USBdriveby
USBdriveby is a cheap pre-programmed Teensy microcontroller emulating a USB drive, mouse, or keyboard. Hackers deploy this device to quickly and discretely install software to override DNS settings for accessing data.
-
PHUKD/URFUKED attack platforms
PHUKD/URFUKED attack platforms work similarly to Rubber Ducky devices. But here the hacker can choose a dedicated time for running the exploit as well as for injecting the malicious keystrokes.
-
-
Maliciously Reprogrammed USB Peripheral Firmware Attacks
-
Smartphone-based HID attacks
In Smartphone-based HID attacks, the hacker creates custom Android gadget drivers to overwrite Android OS functions. When connected to the phone, this infected device emulates the fake appearance of a wireless keyboard or mouse. And, once the connection is forged, the gadget either overtakes the system or steals sensitive information.
-
Hidden Partition Patch
It is a reprogrammable USB flash drive that acts as a regular flash drive. This device, once connected to the system, creates a hidden partition that cannot be formatted, thereby allowing for secret data extraction.
-
Password Protection Bypass Patch
In this case, the hacker makes minute adjustments to the USB flash drive’s firmware device that enable them to bypass password-protected USB flash drives and collect sensitive data from them.
-
-
Attacks based on Unprogrammed USB devices
-
USB Backdoor into Air-Gapped Hosts
These attacks run on the deadly Fanny malware. In these attacks, the hackers use hidden storage with USB to store preset commands. These commands map computers in air-gapped networks and store the data on the hidden storage for future reference.
-
Data Hiding on USB Mass Storage Devices
A form of USB Phishing, this attack involves concealing malicious software or stolen data within a USB flash drive. While storing, the attacker creates a stealth partition that can’t be formatted, thereby enabling hidden data exfiltration.
-
Buffer Overflow Attacks
These forms of attacks start with plugging a USB device into a computer. Once plugged in, the removable USB exploits vulnerabilities in the operating system while processing the device’s functions during enumeration.
-
-
Electrical Attacks
-
USB Killer
The USB attack toolkit triggers an electrical surcharge into a computer causing a short-circuit, which in turn overkills the entire thing.
-
USB Attacks and Cases
Besides the Stuxnet attack, there have been other instances of USB-based attacks either stealing sensitive information or running a malware attack on the system, leading to equipment shutdowns and infections. Here is a list of some of the most notable attacks:
-
Mariposa Botnet (2008)
The Mariposa botnet is a cyber scamming and denial-of-service attack that infected an extensive network of 12.7 million unique IP addresses. This botnet carried an infected USB drive that self-installed itself on a PC to launch an attack. Once installed, it could track the system and collect sensitive information such as bank credentials, passwords, and credit cards.
-
SOGU Malware Infection (2023)
It is a popular cyber espionage campaign that uses a bad USB drive to extract sensitive information from infected hosts. These USB malware attacks target both public and private sector organisations across industries.
-
Equifax Data Breach (2017)
In 2017, some USB attackers exploited a vulnerability in Equifax’s software, thereby compromising the personal data of 147 million individuals.
How UBS Attacks Are Conducted?
Here is a step-by-step guide on how USB Attacks are conducted:
-
Choosing the Target
The journey of a USB attack initially begins with finding the right target. Attackers gather information about their potential victims through various platforms such as social media, websites, and other sources to build a profile. They hunt out the vulnerabilities and then launch various attacks like social engineering or phishing scams to steal their confidential information.
-
Exploiting Vulnerabilities
Once the hacker has targeted the potential weakness of the victim, they move on to exploit them for unauthorised access to their system.
-
Breaching and Data Exfiltration
Once access is gained, the scammer delves deeper into the system to access sensitive data. After locating the information, they either move the information to remote servers or use external servers to maintain control over the compromised system.
-
Subversion and System Manipulation
While breaches focus on stealing information, subversion attacks take a more covert route. Attackers manipulate systems or data to cause disruption or chaos.
Mitigating USB Attacks
As we’ve delved into the intricacies of USB attacks and how they unfold, it’s time to focus on strategies to effectively counter these threats. Mitigation involves a combination of robust cybersecurity measures, employee education, and strategic incident response procedures.
-
Advanced Cybersecurity Measures
Protect your system or device with advanced cybersecurity measures like the latest anti-virus software and multi-factor authentication. Make sure to run regular security assessments to stay updated about the current status of security. Also, you must run regular software updates to fix existing security vulnerabilities on time.
-
Employee Training and Awareness
Business organisations should run regular training sessions to educate employees about common threats like phishing and social engineering. These awareness sessions will help them to recognize and respond to suspicious activities before it’s too late.
-
Incident Response and Recovery
Develop a comprehensive incident response plan that outlines roles, responsibilities, and steps to take in the event of a cyber incident. Also, you should run USB Drop Attack Simulation through drills to ensure your team is well-prepared to respond effectively.
-
Use USB Data-Blocker
A USB Data-Blocker is a physical device that blocks unauthorised access to your computer when you plug in a USB drive.
Conclusion
Truth be told, malicious USB attacks are fast becoming a harsh reality. What’s worse, these virus or malware-laden devices look the same as your regular USB stick. Thus, businesses have to be slightly more careful while dealing with USB sticks today to fight against USB attacks. However, by installing strict cybersecurity measures, these private organisations and government agencies can secure their defences against these incidents.
Be aware of such incidents and stay protected from online attacks. Start your cyber awareness journey with DataSpace Academy. Join our beginner-friendly ethical hacking course now!
 1.12L
1.12L




































































































