White Hat vs Black Hat Hacker: The Ultimate Comparison
Last Updated : 14 Sep, 2024
 52.58K
52.58K

Introduction
In the ever-evolving world of cybersecurity, understanding the distinctions between white hat vs. black hat hackers is crucial. ‘Hacker’ is the most feared term in the cyber world for obvious reasons. Having said that, it’s also to stress that everything comes with both good and bad aspects, and so does hacking. White hat and black hat hacker is the different sides of the same coin and serve different purposes. But many aren’t aware of the good side of hacking and how mastering this skill can land someone their dream job, provided their intent is right.
This blog will delve into the motivations, methods, and impacts of these types of hacker types, shedding light on their roles in the complex landscape of cybersecurity.
Who is a White Hat Hacker?
White hat hackers are also known as ethical hackers. Their primary objective is to detect network vulnerabilities in networks and software before black hat hackers can detect them. They report the vulnerabilities to the management and also recommend remedies.
White hat hackers are also deployed in vafrious related job roles, such as – penetration testers, cyber security analysts, security engineers, information security managers, security consultants, computer security analysts, and Offensive Security certified professionals. They are hired full-time, or as freelancers. Some of the popular white hackers are Tsutomu Shimomura, Charlie Miller, Richard Stallman, and Tim Bernes-Lee.
How to Become a White Hat Hacker?
Aspiring ethical hackers have various options to get their aspiration on the right track. Beginners can sign up for diploma courses in ethical hacking or pen testing to start learning from scratch. These courses cover fundamentals of ethical hacking and offer hands-on training on penetration testing for web applications, mobile applications etc.
White hat hackers can further advance their career prospects through various global certifications. These Certifications are issued by esteemed global cybersecurity regulatory bodies like EC-Council, CompTIA, and so on. C|EHv12 by EC-Council is one of the most sought-after global certifications in the cybersecurity domain. The program has 20 modules, encompassing more than 300 attacks and 2000 hacking tools. After completing C|EHv12, you can enroll for the C|PENT Certification as well. This Certification is also issued by the EC-Council.
Who is a Black hat hacker?
Black hat hackers are infamously known as unethical hackers. They are the ‘bad guys’ of the cyber world, accused of unauthorised access to networks and systems. Driven by malicious intent, they steal sensitive personal and financial data to either sell on the dark web or ask for ransom.
Black-hat hackers are usually motivated by personal gain, financial incentives, criminal purposes, or employment by rogue states. They often operate alone or with others who have similar malicious intentions. Kevin Mitnick, Vladimir Levin, Adrian Lamo, Gary McKinnon, and Jonathan James are some of the infamous names on the list.
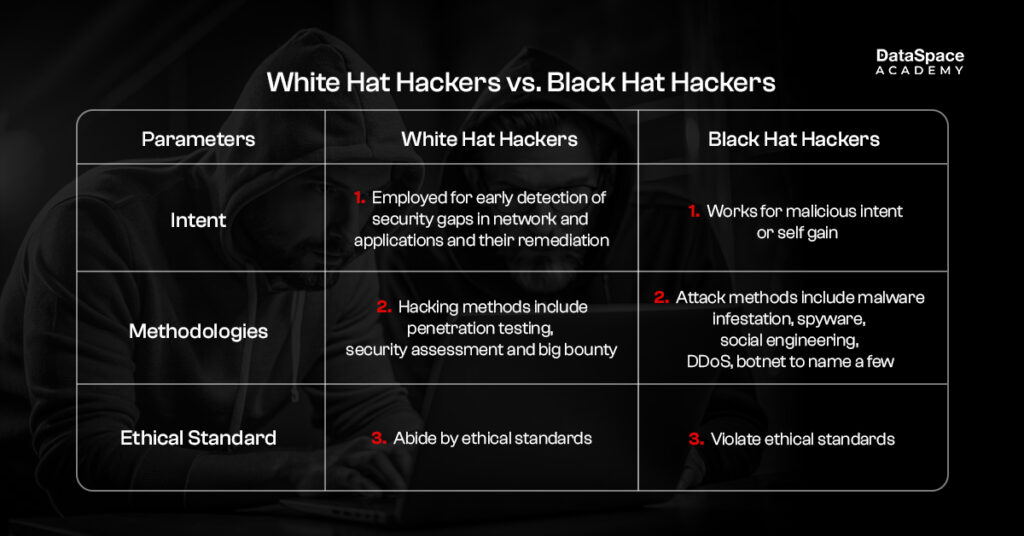
Differences between white hat hacker and black hat hacker
White hat hackers are the ‘good guys’ of the cyberworld , while black hat hackers are the ‘bad guys’.
The principal difference between them is the “intent”. Black hat hackers break into networks to “steal” confidential data for their illicit gains. But, white hat hackers “penetrate” into networks to detect security vulnerabilities in a system or application. Their intent or goal is always to protect organisations from black hat hackers through early detection and remediation of security vulnerabilities. Thus, unlike black hat hackers, white hat hackers always have the permission to penetrate a network to examine the security loopholes.
Let’s uncover the good vs. bad in the featured differences below:
Conclusion
White hat hackers and black hat hackers have similar skills but operate differently. Mastering ethical hacking can unlock limitless job opportunities for qualified professionals in the ever-dynamic, challenging, and promising cybersecurity landscape. Candidates looking to master these in-demand skills must sign up for industry-leading cyber security courses online. Make sure the chosen course offers hands-on training to help you develop practical experience.
 52.58K
52.58K




































































































